TL;DR WordPress security issues are a common concern, and outdated plugins or themes are often the main reason behind successful attacks. In this article, you’ll learn how WordPress websites get hacked, what the consequences may be, and which popular plugins recently had vulnerabilities (Contact Form 7, Easy WP SMTP, Redux). You’ll also find out how tools like WordPress Toolkit, ImunifyAV, and Imunify360 can help keep your website safe, and what to do immediately if your site has already been compromised.
WordPress and issues related to its security are common notions occurring in questions from our clients, and therefore a regularly appearing topic on our blog. Last weeks have brought many bad events – websites based on WordPress have been hacked all over the world due to “leaky” plugins.
Read how to find out what happened and how it might apply to you.
How WordPress is hacked?
Our clients very often write to us “but I haven’t done anything with my website for the last 5 years”. Unfortunately, most often this is the cause of hacks.
What could have led to the hack:
- An outdated version of your WordPress.
- Outdated installed plugins.
- An outdated theme.
- Malware attack, that infects your PC and steals the password to your website hosting account.
- Using the same password on various services and the leakage of password from a different service.
- Keeping another, “leaky” WordPress site on the server, for example, an old version of a page from 2009 in the “old” folder.
- Keeping on the server the software other than WordPress which has leaks (e.g. outdated Drupal).
Remember that the password cannot be leaked on our side. The reason behind this is we, as a service provider, don’t keep your login passwords. Instead, we store their cipher and password verification is undertaken through the comparison of ciphers, not passwords.
What can be the consequences of a hack?
After a successful attack, a hacker places on your account an executable file which gives a possibility to change any other files. The hacker may spread malware all over your account, modify the existing files, add malicious cron jobs, and so on. Such code is most often encrypted so it will be difficult to trace the principles of its operation.
Our observations show that most attacks are not aimed at a specific website. Break-ins to steal data are not so common.
The most common effects of gaining unauthorized access to your WordPress installation are:
- Sending spam from your email accounts. The attackers often send many thousands of emails advertising fake financial services or including download links for malicious software. This type of spam greatly damages your domain’s reputation and can mark your emails as spam.
- Malware distribution. Websites encouraging to install the unknown programs are placed on your domain. Links to them are then “advertised”, e.g. in social media.
- Spam SEO. There are new subpages on your website with positioning links to others. The attackers use the reputation of your website for their purposes.
- Website destruction. The attacker may delete a part or all files “for fun”. In this case, recovering them is usually possible from a backup.
- Personal data leakage of your website. This is the worst-case scenario – it is associated with high penalties resulting from legal provisions.
Popular plugins with vulnerabilities in December 2020
Contact Form 7
Contact 7 is a very popular plugin for creating various application forms on websites based on WordPress. Most often it is a contact form. The plugin is easy to use, used by more than 5 million websites in the world.
On 16 December 2020, the error description with the CVE-2020-35489 code was published. A vulnerability was found in 5.3.1 and earlier versions of this plugin allowed to place any file on the server without any authorization. It allows the attacker to have full access to a given website hosting account.
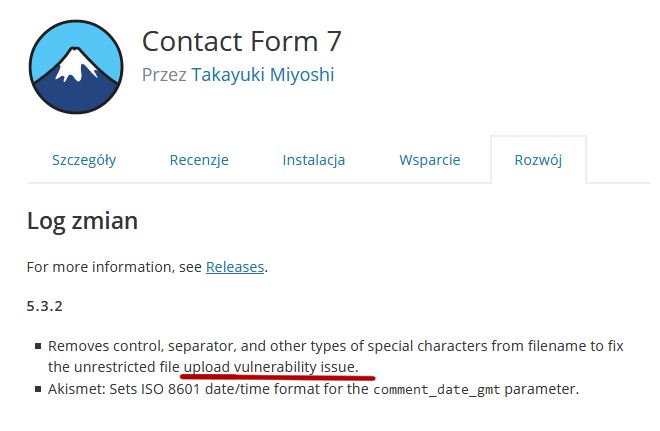
The new 5.3.2 version of the Contact Form 7 plugin was immediately released which fixes this issue. Users of this plug-in should update it as soon as possible.
WordPress Easy WP SMTP Plugin
WordPress Easy WP SMTP Plugin has half a million active installations. The plugin allows you to force WordPress to send all emails using SMTP – so not from PHP level but similar to an email client. It increases the delivery level of emails.

It is true that error in the plugin is not as important as in the case of Contact Form 7, but it allows to list all files in the folder in which it is placed. It allows finding a log file that can contain information about WordPress admin panel login. The attacker calls the administrator password reset and then he finds the password reset code in the log file.
This vulnerability has been removed in version 1.4.3 of the Easy WP SMTP Plugin.
Redux Plugin
Redux is an extension with over a million active installations. It expands the possibility of Gutenberg editor in various templates. It allows for the easy creation of great-looking websites in WordPress thanks to a library of more than 1,000 finished templates for self-adaptation.
The detected vulnerability is of the CSRF type (Cross-Site Request Forgery). It allows the attacker to use the authorizations of the currently logged-in user (administrator) to send commands without the knowledge of this user. WordPress has a so-called “nonces” mechanism, one-time tokens to authenticate requests. As it turns out, Redux has been verifying the correctness of nonces only when they appeared in the request. In the case of their absence, the request was simply executed.
This vulnerability was patched on December 12, 2020, in version 4.1.24 of this plugin.
Automatic updates using WordPress Toolkit
Since November 2020, WordPress Toolkit has been available on our servers. It is a tool both for a simple installation of any WordPress domains connected to your server as well as for managing existing updates.
WordPress Toolkit allows among others for automatic updates of your WordPress and all add-ons.
To switch on this option, log in to the server administrator panel (cPanel) and go to WordPress Toolkit. You will see a list of all WordPress installations on your account. Each of them has an “Autoupdate settings” switch. Here you can update WordPress, plugins, and themes. We recommend enabling all those options.
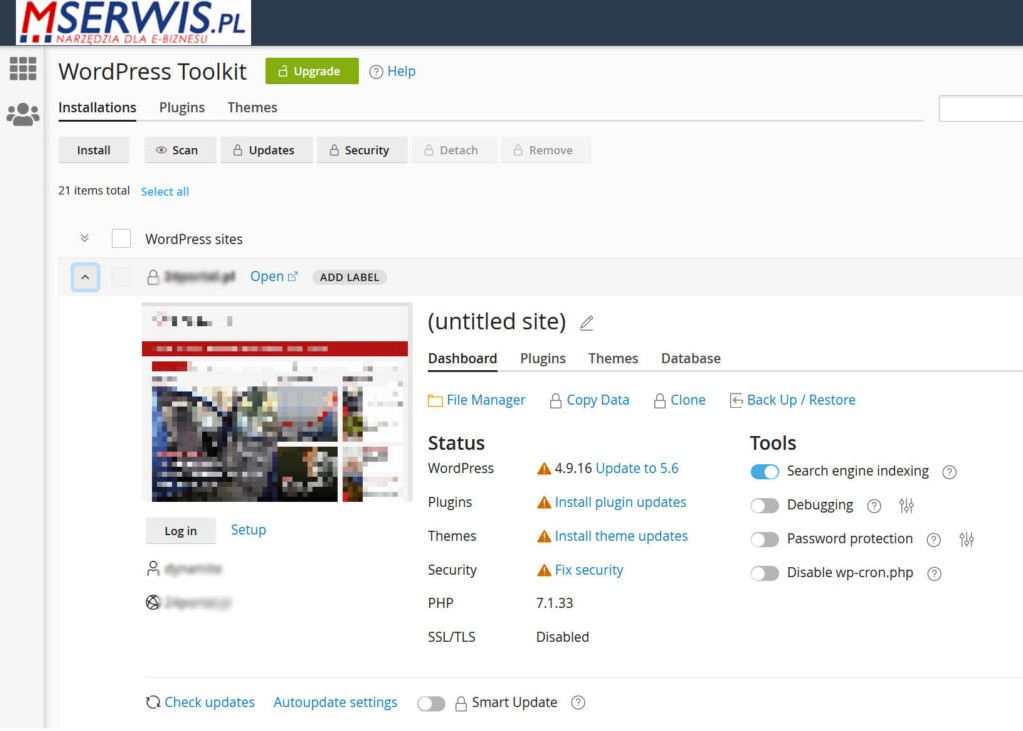
If there is an update of a given plugin related to security, WordPress Toolkit will update it without manual action. Thanks to this, your website will be safe. Is it cool? Sure it is.
My WordPress has been hacked – how to go with it?
You have to act as soon as possible. Each day of delay means losses resulting from the lack of website operation and also decrease in SEO position, including even a threat of complete removal of the website from Google index.
The hosting provider is obliged to immediately block a hacker in case of a hack. It usually means blocking access to the entire WordPress installation. However, access is still possible from the cPanel or FTP level.
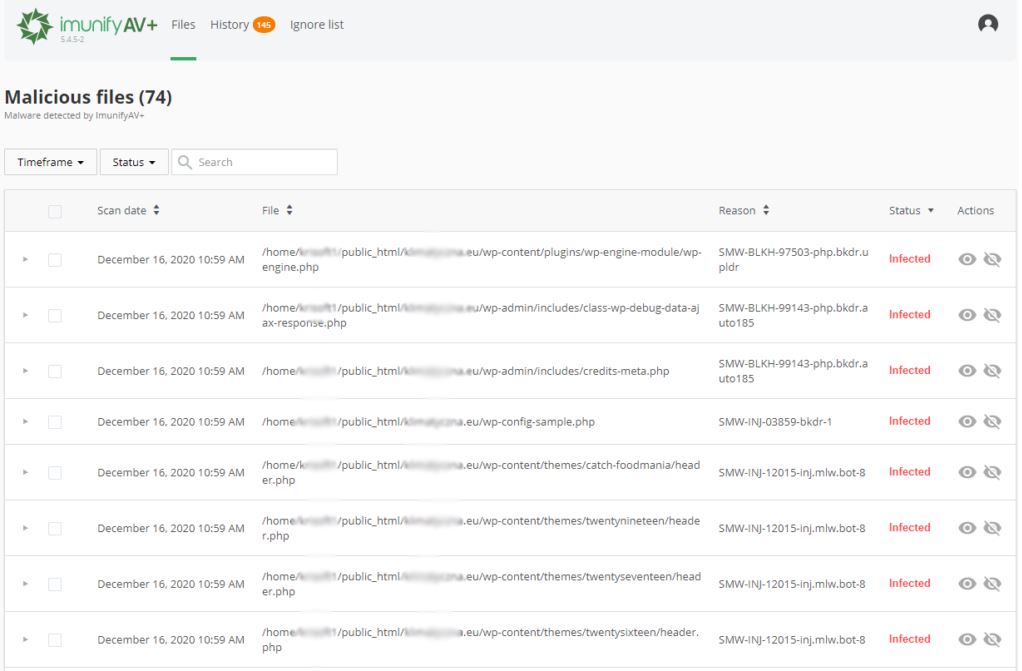
Using antivirus scanner ImunifyAV, you may find all infected files on your website hosting account:
You can also use Imunify 360. It’s proactive protection that helps to prevent the majority of attacks. However, if a hack occurs, Imunify 360 will automatically clean or remove the malware.
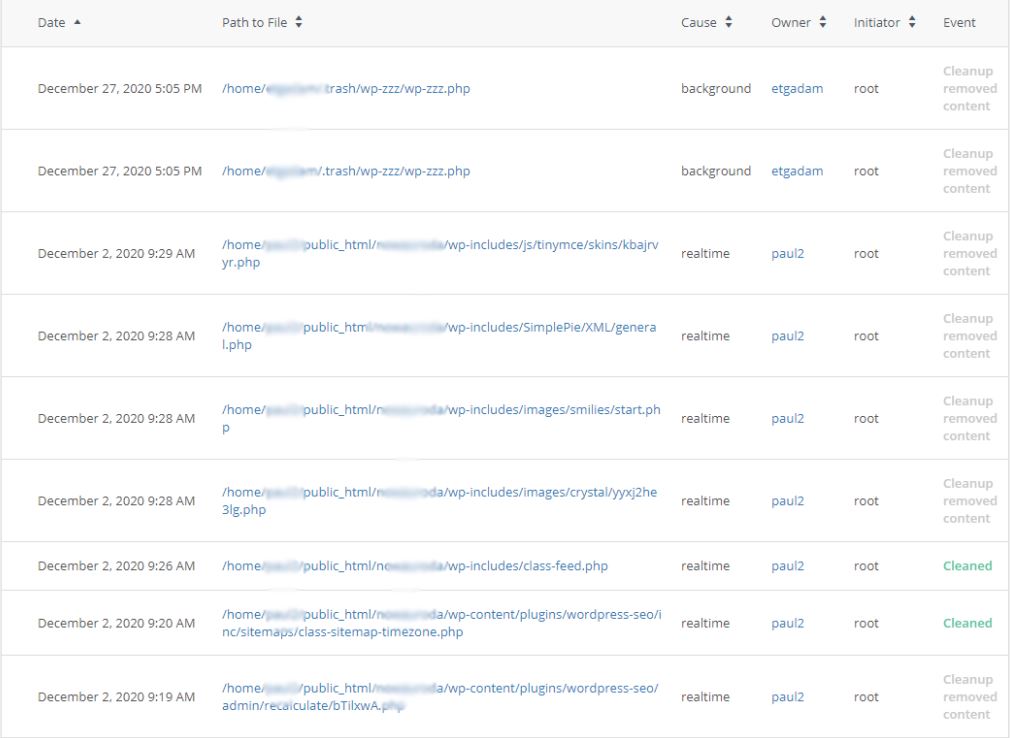
However, just removing the malicious files may not be enough. You need to obtain access to the WordPress panel in an isolated way, to perform necessary clean-ups and updates, and also solve the problems arising from the attack.
FAQ
Why do WordPress sites get hacked?
Most attacks result from outdated plugins, themes, or WordPress versions. Other causes include weak passwords, malware-infected computers, or leaving old “leaky” sites on the server.
What are the most common consequences of a hack?
A hacked site may send spam, distribute malware, host spam SEO pages, or even leak personal data. In severe cases, files may be deleted.
How can I protect my WordPress from hacks?
Enable automatic updates with WordPress Toolkit, regularly update plugins and themes, and use security tools like ImunifyAV or Imunify360.