TL;DR The Dark Web is often surrounded by myths, but in reality, it’s just a hidden part of the Internet that requires special tools like the Tor browser. In this article, you’ll learn what the Dark Web is, how it works, what you can find there, and how to access it safely. We also explain the difference between the Surface Web, Deep Web, and Dark Web, along with the main risks to be aware of.
Each of you must have heard about the mysterious, hidden Internet. Dark web owes its reputation to techno-futuristic movies from the 80s and 90s, and to Keanu Reeves in black sunglasses in unforgettable Matrix. The darknet also owes its mystery to TV, which trivializes and oversimplifies the picture of our reality to a greater extent. In this article, we would like to introduce a few interesting pieces of information about this hidden part of the Internet. It won’t be any secret knowledge, just a handful of proven facts and in the end – some pieces of advice.
What is the Dark web?
A few years ago, Krzysztof Lech in “PR World”, suggested the most adequate definition that we’ve managed to find:
“Dark web is a term that strictly relates to websites hiding the IP addresses of the servers which they use. They can be visited by any Internet user, but it is very difficult to determine who is behind them. These pages can not be found with regular search engines. The ones who act as a part of the Dark web, hide their identity. They do this primarily by using the Tor encryption tool (The Onion Router), which most Internet users have probably heard of mainly in the context of end-user hiding properties.”
Or as we can read on Wikipedia:
Onion routing is implemented byencryption (…) nested like the layers of an onion. Tor encrypts the data, including the next node destinationIP address, multiple times and sends it through avirtual circuit comprising successive, random-selection Tor relays. Each relay decrypts a layer ofencryption to reveal the next relay in the circuit to pass the remaining encrypted data on to it. The final relay decrypts the innermost layer of encryption and sends the original data to its destination without revealing or knowing the source IP address. (…) Tor is not meant to completely solve the issue of anonymity on the web. Tor is not designed to completely erase tracks but instead to reduce the likelihood for sites to trace actions and data back to the user. (…) Tor cannot and does not attempt to protect against monitoring of traffic at the boundaries of the Tor network (i.e., the traffic entering and exiting the network). While Tor does provide protection against traffic analysis, it cannot prevent traffic confirmation (also called end-to-end correlation).
For example, the US government can monitor any broadband connection to the Internet (under the 1994 CALEA Act), therefore it can control both endpoints of Tor connections made on its territory.
In Poland, the legal tool allowing for the identification of Tor network users is the European Union Directive 2006/24 / EC on telecommunications data retention.
Data retention is the routine procedure to log and store information about who connects with whom and when (or tries to connect) done by the operators using means of electronic communication. According to the Telecommunication law, the operators are obliged to store the data for two years – for purposes related to public security – and share them with authorized institutions.
The history of the darknet hides many more attempts – both theoretical and practical – of identifying anonymous users of the Tor web.
The websites that we know from the “normal” Internet, work on Tor in a form of hidden localization. These services are available via the top-level Tor’s pseudo-domains – .onion. What do they look like?
http://rzb5nlpvy5oqnket.onion/ – this is, for example, the address of the Panoptykon Foundation in the hidden web. One of the goals of this organization is to protect human rights in the surveillance society.
It is worth remembering that the .onion domain in the Tor web is a part of the ICANN register, and you cannot connect with it without using TOR. Because of the names of the websites, which are difficult to remember, the majority of users use the index of websites available on Google or other search engines.
When it comes to the darknet, its size may be surprising. According to different studies the “official” part of the web, e.g the one that can be found using popular search engines, constitutes only a small percentage of the whole thing. What is the real web size then? Let the following graphic be the answer:
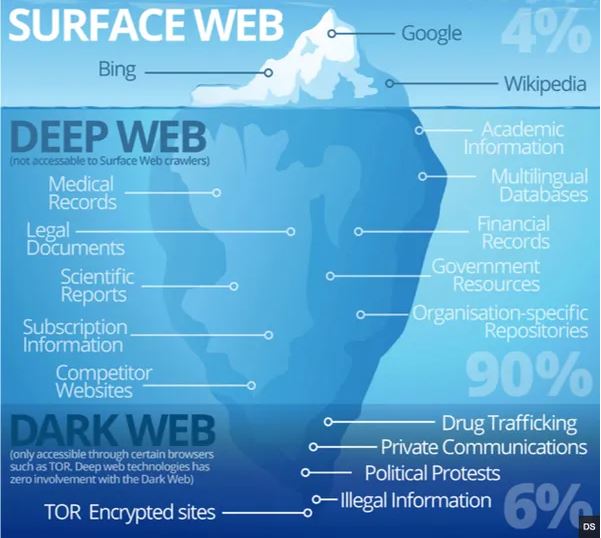
Like any other depth, the darknet also has its degrees of “depth”. The websites at the very bottom are considered to be the most hidden and most secure. Conspiracy theorists have even coined the term Mariana’s web – the depth level of Mariana Trench – the deepest known place on Earth. According to the supporters of this theory, it would include the most secure and darkest secrets of humanity, and you can access it only through quantum computer technology. Welcome to Dan Brown’s world. But let’s go back to the surface for a moment.
How to access the Dark Web safely
In fact, it’s not hard at all. A web client named Tor Browser is all we need to connect to the Tor web. After installing the package you can enter any website on the .onion domain. Main part of the Tor Browser, among others, is a built-in modified Mozilla Firefox ESR web browser. For more info on how to use it see the video below:
What can you find on the Dark Web?
The dark web, as a place of unrestricted freedom, can be used for myriad of illegal activities including blacmailing, gambling, buying weapons, drugs, child pornography or terrorism. But that’s only one side of this web. On the other hand, it is a place where people can gather, organize and exchange information outside the radar of those who repress them.
The good example is one of the biggest players on the online market – Facebook, which launched its service on Tor three years ago. As reported by Antyradio: In April 2016, for the first time in history, the number of users logging into Facebook via the anonymity web exceeded one million. They are most likely people from countries in which access to Western websites is blocked.
Risks and dangers of using the Dark Web
If for any reason, you decided to check what is on the other side, be sure to check the following tips:
- Tor can be dangerous if misused, like any other thing;
- Don’t provide your real data;
- The people using Tor want to be anonymous and many of them may fake their real identity.
- Tor is constantly monitored by the police who may deliberately encourage illegal activities.
* In the article I used the names dark web and darknet interchangeably because I don’t see any significant difference between them.
FAQ
Is the Dark Web illegal?
Not entirely. Accessing the Dark Web with Tor is legal in most countries. What is illegal are the activities often associated with it, such as buying drugs, weapons, or stolen data.
What can you find on the Dark Web?
Apart from illegal markets, the Dark Web also hosts forums, whistleblower platforms, and even official sites like Facebook’s Tor version, used in countries with restricted Internet access
Is using the Tor browser safe?
Tor increases anonymity but does not guarantee complete security. Users should avoid sharing personal data, downloading unknown files, and clicking suspicious links.