Did you receive an e-mail with information that your account has been hacked? The hacker threatens to reveal embarrassing recordings from the webcam of your computer, on which you watch pornography? Is he demanding a ransom for “keeping a secret” and not sending the videos to your colleagues? Most likely you have fallen victim to fraud, therefore, don’t fulfill the demands and don’t send money – at first, check who is the actual sender of the email. The below tips will help you.
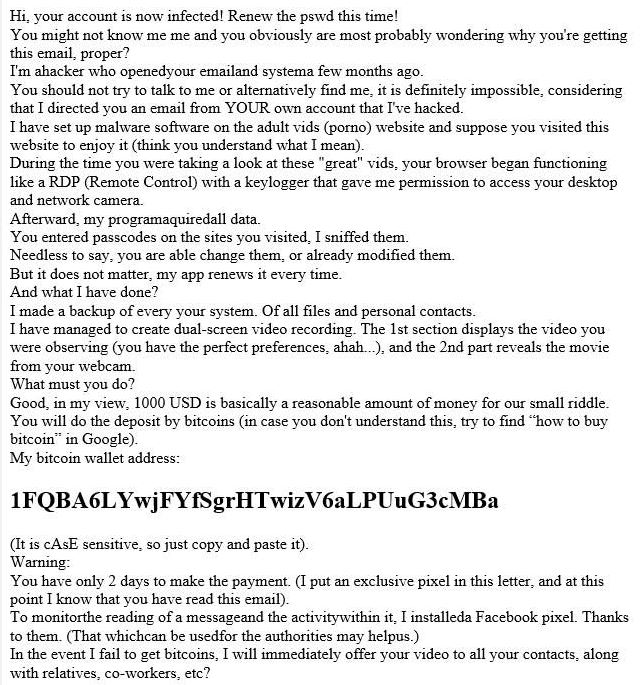
With such e-mails, the scammers try to extort data or money.
Is it possible that a hacker broke-in into my email box and send me an e-mail?
“A hacker”, who rather should be referred to as a scammer, didn’t hack your account, but only faked the sender’s address. The tools allowing to change the sender are available on the Internet for free. In such a case, the scammer only needs to know your e-mail and very often it is available to the public. Spammers take advantage of this scam to extort confidential data or, as in that case, money. Such fraud is called spoofing.
Can I check who the real sender of the email is?
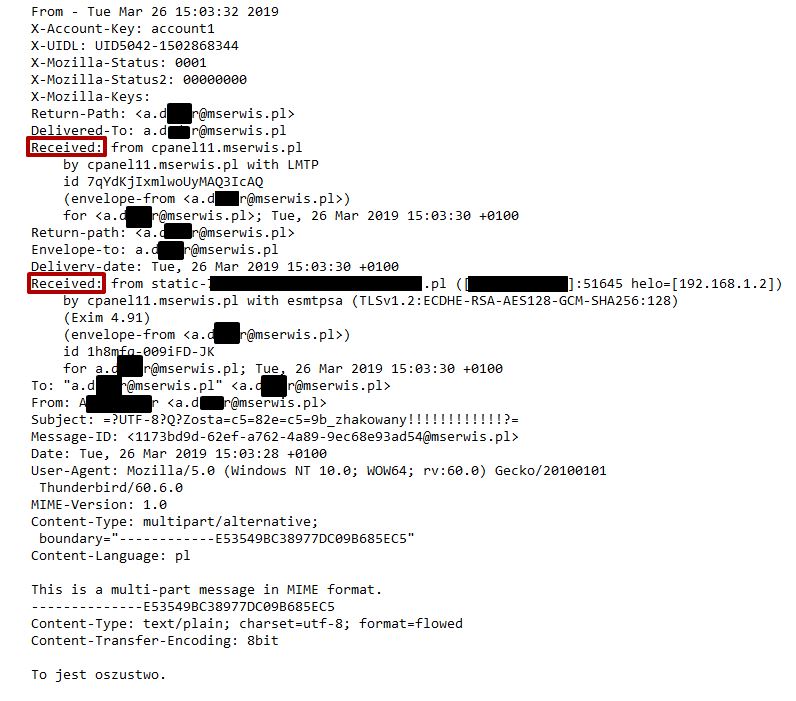
You can detect false e-mail by checking the headers of messages. The most important information is in the “Received” section. It concerns the e-mail server from which the message was sent. If this is not the server responsible for handling e-mail on your domain, you are dealing with a scam.
How to check the headers of messages?
Gmail
Open the message and click the button “more” on the right side of a screen. Select “Show Original” from the menu that appears.
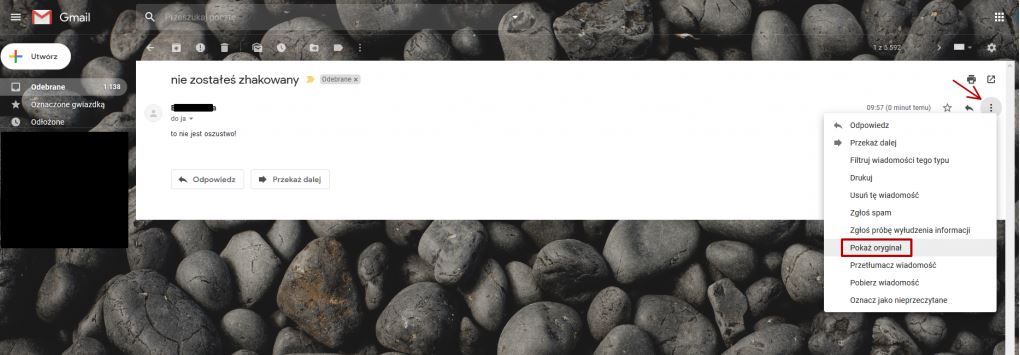
The header will be displayed in a new window.

Thunderbird
Open the message and click the button “Other” on the right side. Select “View Source” from the drop-down list.
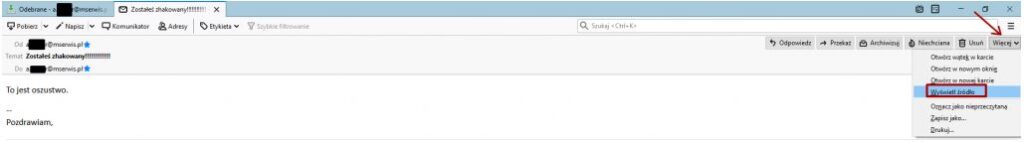
The header will be displayed in a new window.
Outlook
Open up a message. Click on “File” in the top menu, then select “Properties”.
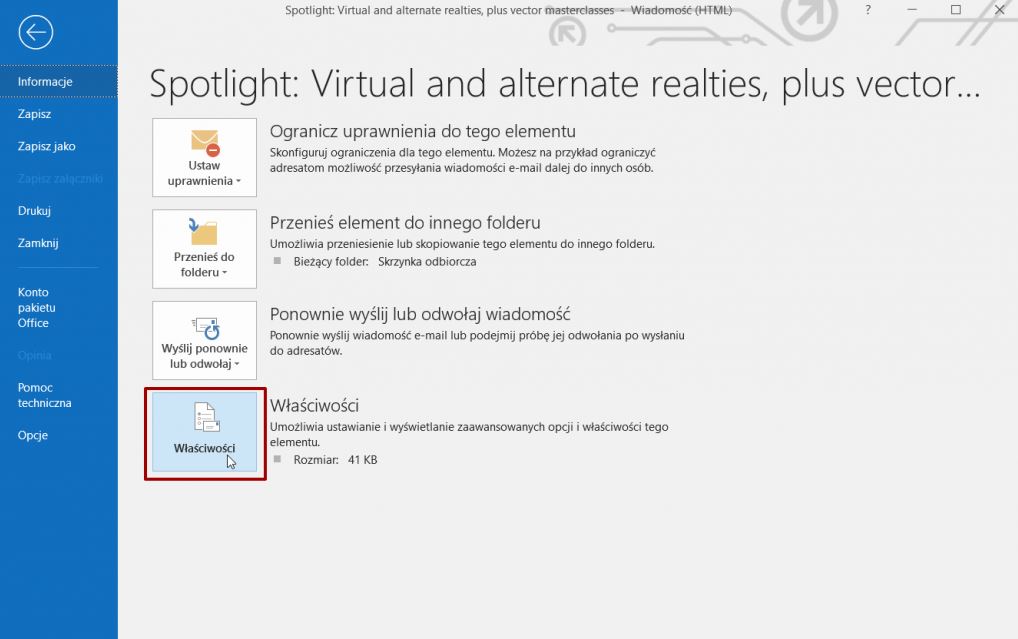
The header will be displayed in a new window, at the bottom of a page.
Fake e-mails
All the examples so far have shown the headers of e-mails sent by real and trusted senders. What do the headers of messages from a scammer look like?
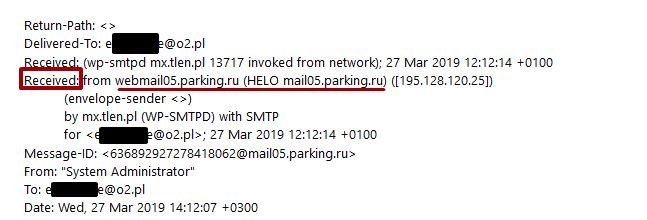
The e-mail wasn’t sent by the email server but by the other one – from Russia. The message is from a scammer.
“Break-in” on the mailbox – summary
Spoofing is one of the most popular scams which happen in e-mails. The scammer supposedly sends a message from your e-mail address to your inbox, because of that you may think that he hacked your account. In fact, he sends an email from a completely different server and doesn’t have access to your email. For such a scam just an e-mail address is needed, that’s why it is so popular.
You can check which server sent the message. You will do it in the message headers. The key header is “received” – there is information about the server from which the sender sent the e-mail. If this is not the server responsible for handling e-mail on your domain, you are dealing with a scam. Now you can safely delete the message.
The following website https://ripe.net can help with the identification of a sender, this website allows to search the worldwide databases of IP addresses. The server’s IP address is one of the elements of a header analyzed above.
After entering the website, type in the top left corner e.g. 193.17.41.99, and click on a search symbol. Additionally, you can choose to search in all available databases (Search resource objects in all available databases).
In the netname box, the name of the company which uses or shares a given internet connection (e.g. O2-NET), country symbol, and other additional data will be visible. One should remember that legally operating e-mail server operators don’t have any reason to hide their data in such databases, thus we can easily identify the e-mail of a sender and legally operating a server of the e-mail account administrator. This will allow us to check whether the mail was sent from our e-mail server.
This can only happen when we use the same e-mail password for different places on the web (e.g. different online stores). The password together with an e-mail may trickle out, for example, from a poorly protected online store.